See Every SaaS Tool, Even the Ones IT Doesn’t Know About
Discover and manage Shadow IT through real-time, browser-native visibility.
Most security teams rely on identity providers (IdPs) and SSO logs to track SaaS usage, but that only works for sanctioned apps. In reality, employees adopt new tools every day without IT oversight. These unsanctioned apps, often called Shadow SaaS, introduce serious compliance and security risk. Neon Cyber offers SaaS risk visibility beyond your identity provider capturing unsanctioned app activity right from the browser.
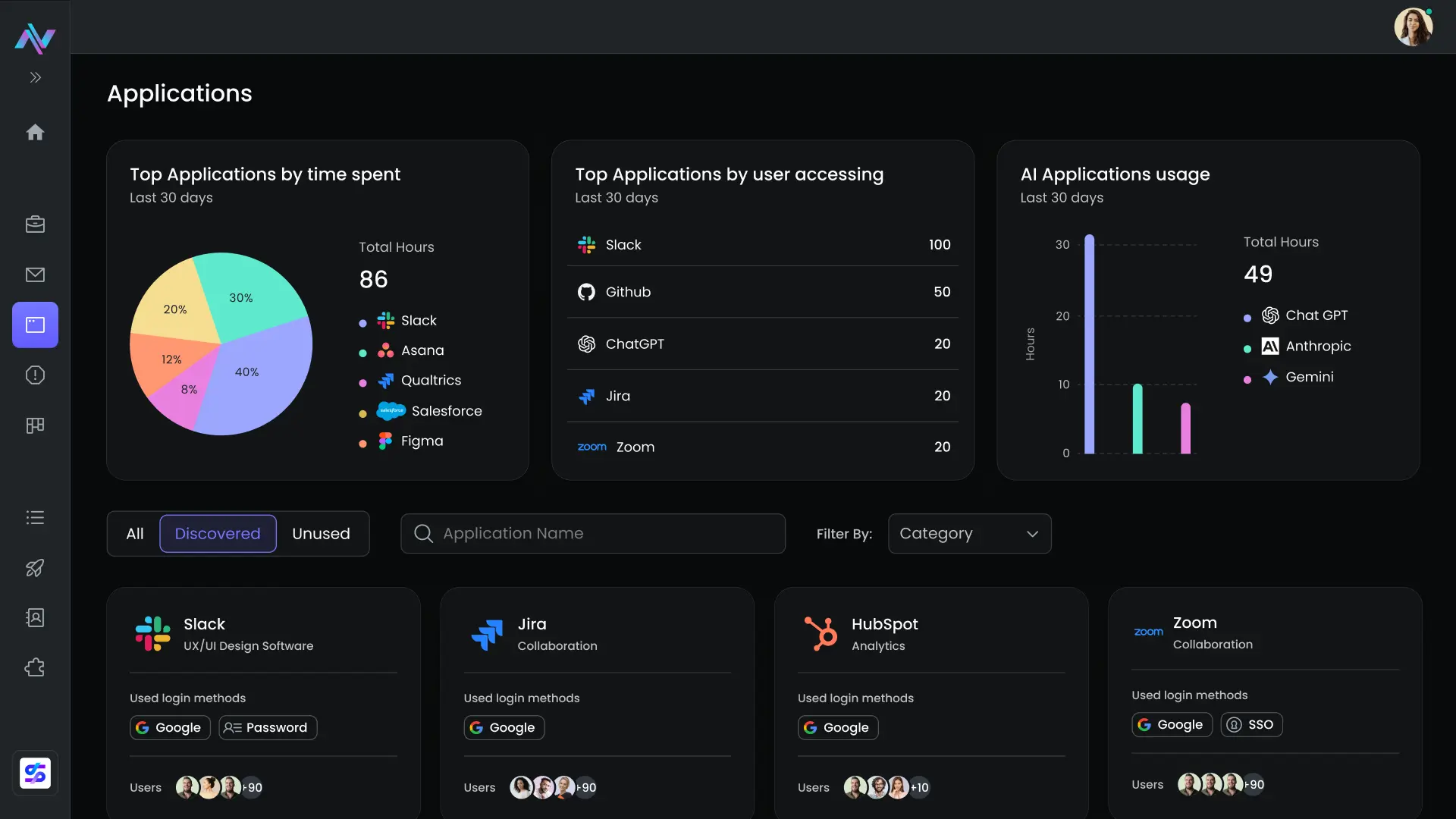

Traditional SaaS Discovery Methods Fall Short
Today’s attacks live in browser sessions, not just networks. Instead of reacting to alerts after the fact, Neon takes action in real time—right where users work.
IdPs can’t see apps users don’t register
CASBs miss tools without network traffic
EDR can't see web page logins
Complexity with integrations and lack of resources limit observability. Neon makes it easy.
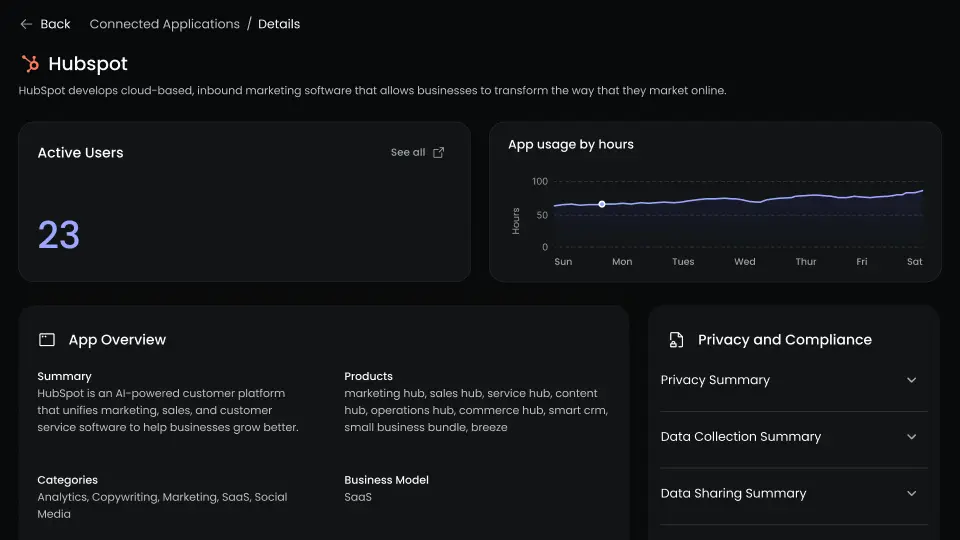
Shadow SaaS Problems?
How Neon Finds Hidden Tools
Shadow SaaS grows fast and without visibility, risk goes unmanaged. Neon deploys a browser-native agent that powers our SaaS Application Catalog, an always-on inventory of every web-based tool your workforce touches, with no integrations required.
Maps Browser-Based SaaS Usage
Tracks user activity to discover all tools in use, whether they’re connected to SSO or not.
Flags Unsanctioned or Risky Tools
Surfaces unknown, unapproved, or non-compliant vendors along with context like usage volume, access frequency, and user role.
Scores Vendors for Compliance Risk
Provides compliance data, regional hosting, and risk levels for every discovered app.
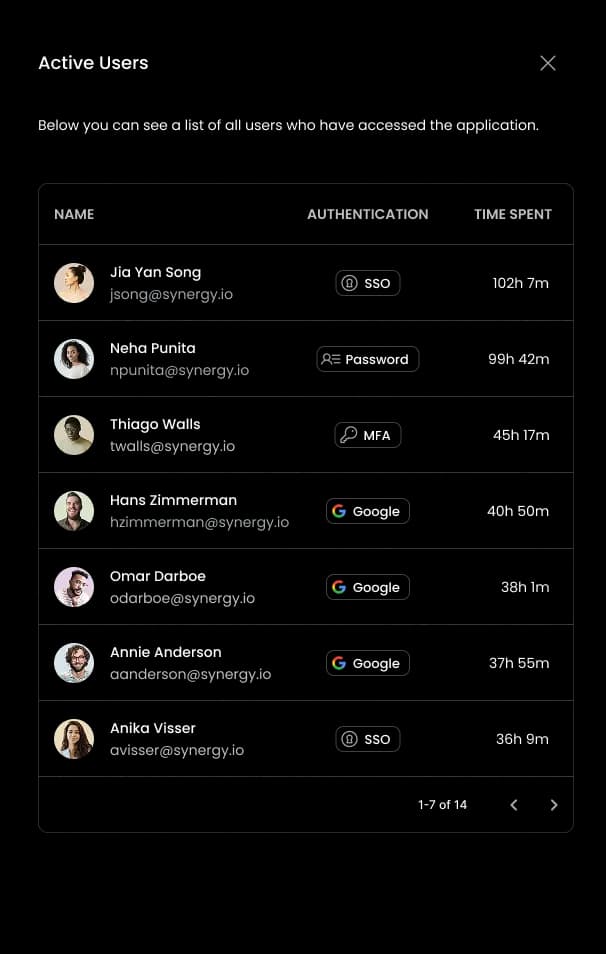
Use Case Sample
A departing employee signs up for a file-sharing tool using their corporate email. It’s not in the IdP, and no alerts are triggered. With Neon:
The app is immediately discovered via browser session
The tool is flagged as unsanctioned and high-risk
Security is notified, access is revoked, and compliance logs are updated
Result: Shadow IT is identified before it becomes a breach vector.
Discover Your Hidden SaaS Risk in 5 Minutes
Speak with the experts on Shadow-SaaS and Shadow-AI to learn what Neon can do for your team
