Make Authentication Policies Actually Stick
Tackle complex authentication issues quickly without annoying integrations.
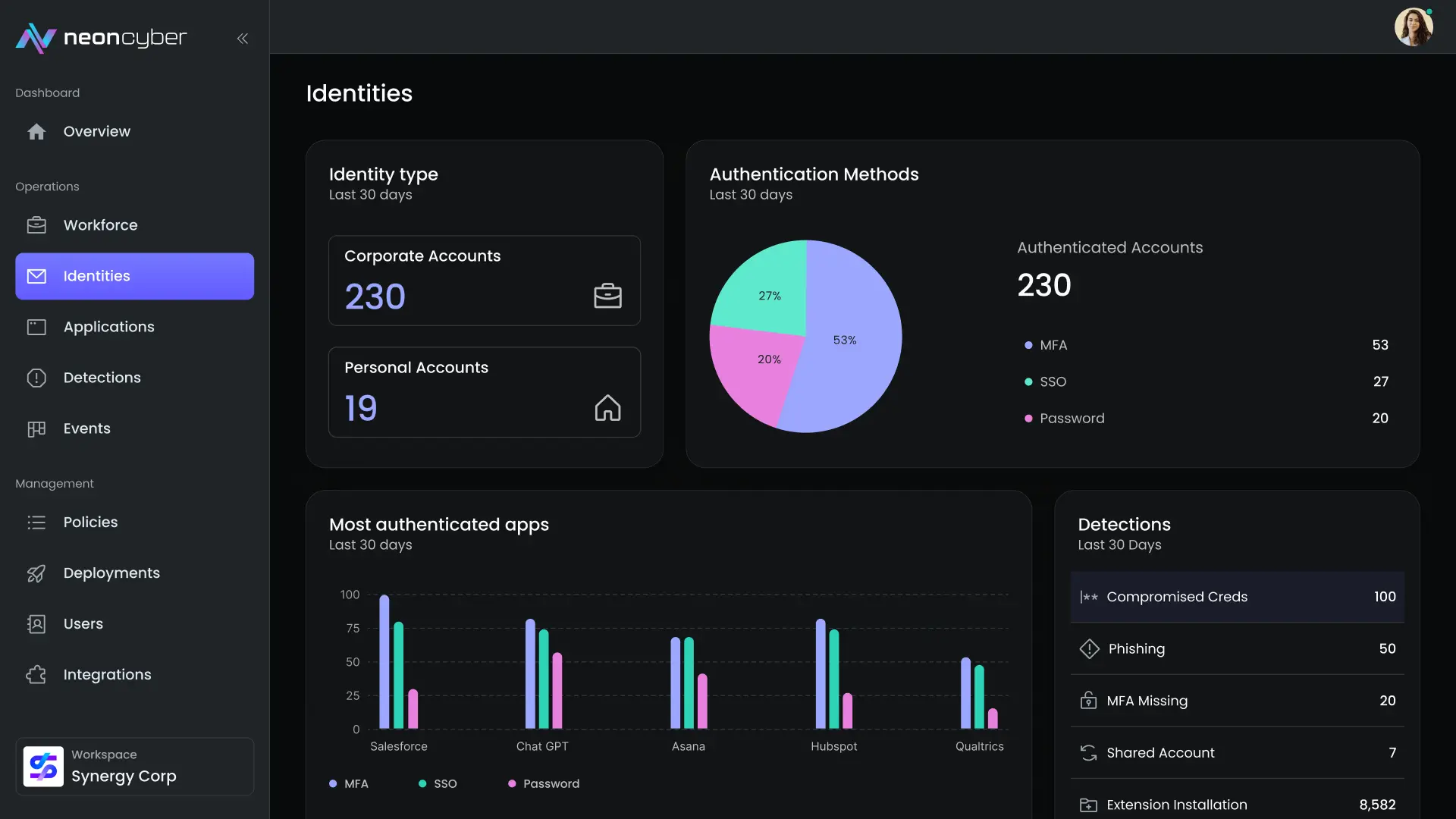
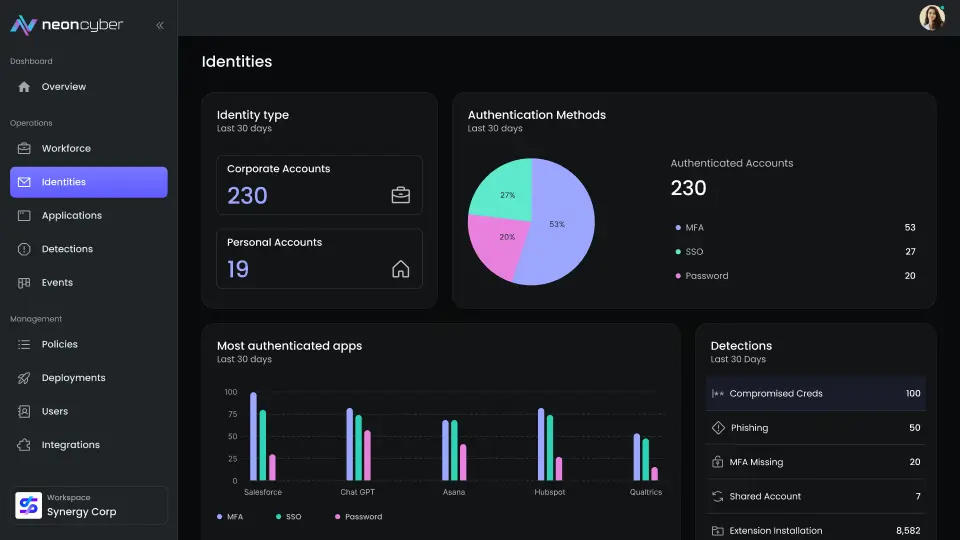
Most companies have solid identity and access policies on paper. But in practice, users skip MFA, reuse credentials, or log in from unsanctioned devices without consequences. These gaps become security liabilities. Neon makes authentication governance real by observing login activity in the browser and enforcing policy at the moment of risk.
Download the Authentication Governance solution brief
Discover how to enforce phish-proof authentication quickly
Download
How Authentication Slips Through
These behaviors often involve tools outside IT’s purview, compounding compliance risk. Traditional identity controls depend on integrations or endpoint agents. But users bypass these systems constantly:
Logging in from unmanaged devices
Accessing unsanctioned SaaS tools
Skipping MFA due to poor implementation
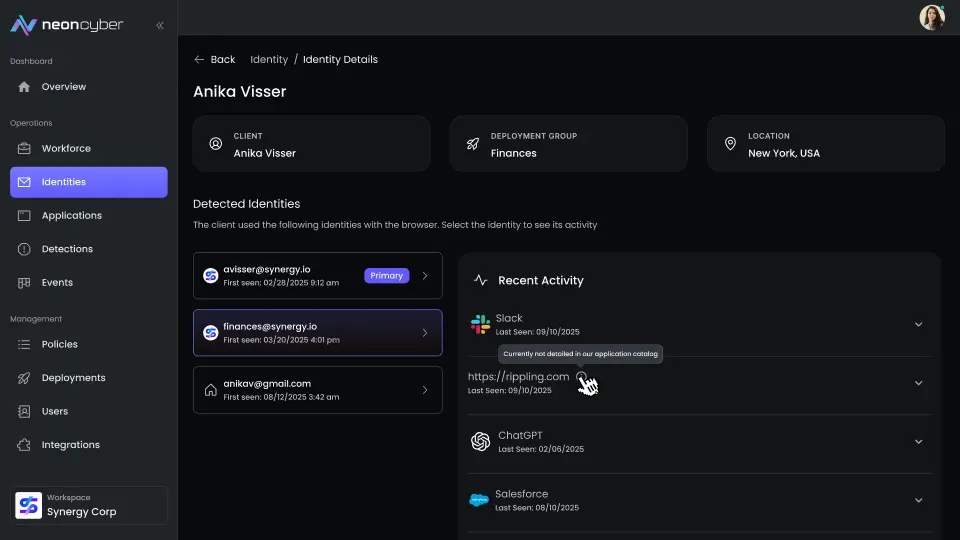
Once logged in, there’s little visibility or enforcement. That’s the gap Neon closes.
Browser-Native Policy Enforcement
Neon runs inside the browser watching how, where, and when users authenticate. It responds instantly when violations occur.
Spot Risky Authentication in Real Time
Neon detects login behaviors that indicate identity risk, including:
- MFA avoidance or failure
- Password reuse across services
- Login attempts from unexpected locations or devices
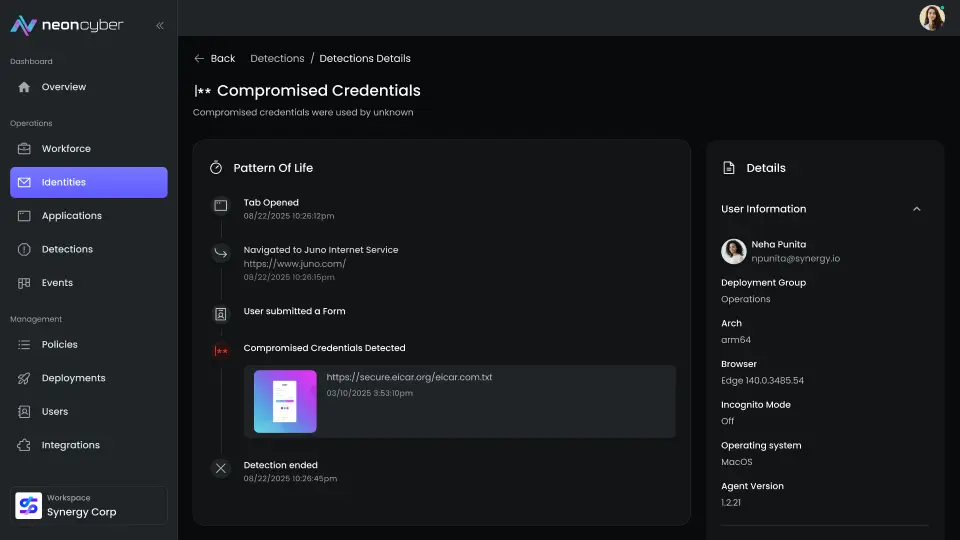
Block Violations as They Happen
When a login doesn’t meet policy, Neon can:
- Block the action entirely
- Prompt the user to re-authenticate
- Log and escalate the event
Upgrade Identity Hygiene Automatically
Every login event adds to your authentication risk profile. Neon identifies:
- Weak patterns across departments or users
- Tools consistently accessed without MFA
- Behavior that puts compliance at risk
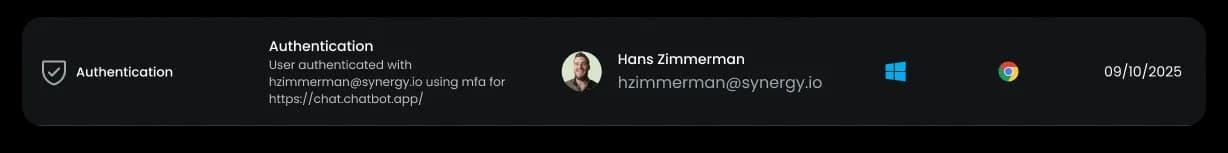
Real-World Use Case
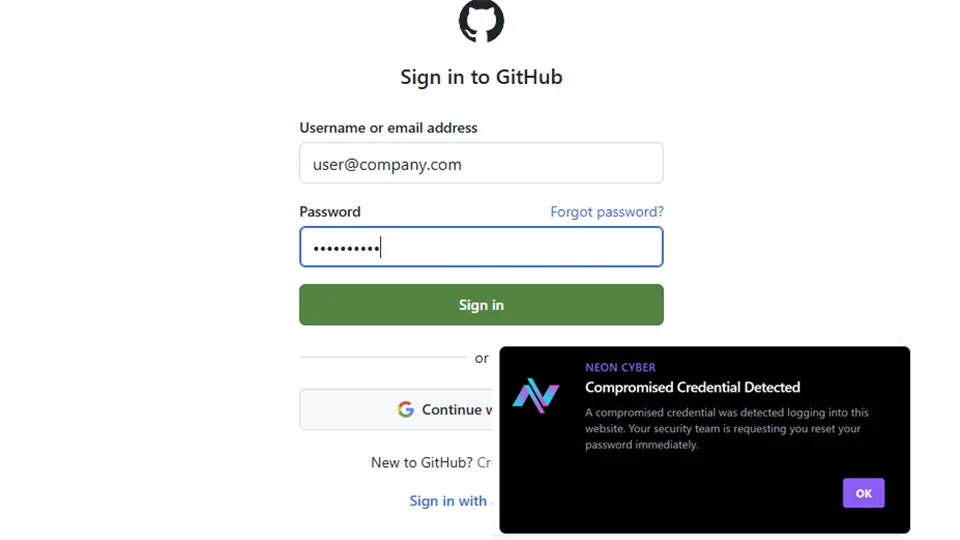
An employee signs in to a third-party AI tool using their corporate email. The login bypasses SSO, and the tool doesn’t require MFA. With Neon:
The login is flagged in the browser
A warning is triggered, and access is blocked
IT receives a real-time alert and logs the event
Result: The policy violation is stopped, and the risk is logged—no manual audit required.
Audit Your Authentication Gaps
Speak with the experts on authentication governance to learn what Neon can do for your team
