Stop Phishing Where It Happens
Catch what traditional email security tools miss right in the browser, in real time.
Most phishing defenses stop at the inbox. But today’s attackers are smarter using trusted platforms, dynamic redirects, and AI-crafted lures to slip past filters. By the time a user clicks, it’s too late. Neon Cyber changes that. Our browser-native protection detects phishing attempts after the click—before damage is done.


Why Traditional Tools Fall Short
Legacy email filters rely on static rules and domain analysis. They can’t keep up with evolving tactics like one-time-use phishing links, credential harvesting hosted on trusted platforms (e.g., SharePoint, Notion), and personalized spear phishing with deepfake content, and once the email is delivered and opened, most tools can’t see what happens next.
Getting Phished?
How Neon Stops Phishing In Action
Instead of relying on logs or alerts, Neon observes activity directly in the browser—right when users interact with risky sites, forms, or logins
Detect Phishing As It Unfolds
Neon’s AI-Powered Phishing Detection Model identifies and stops phishing threats at the point-of-click analyzing both user behavior and threat patterns in real time, directly in the browser. It outpaces traditional tools by combining behavioral telemetry with AI and NLP to spot credential misuse, suspicious links, and unsafe data entry before attackers can act. Using advanced pattern recognition and behavioral analytics, Neon flags suspicious interactions like fake login pages, deceptive UI elements, and credential re-entry requests.
Respond Instantly—Right in the Browser
Neon acts instantly in the browser, no waiting for logs, dashboards, or delayed alerts. It steps in immediately: warning users, blocking the action, or triggering policy enforcement when threats emerge.
Learn and Adapt
Every flagged incident helps improve detection across your organization. Neon builds context over time understanding which behaviors are risky, which are normal, and how attackers evolve.
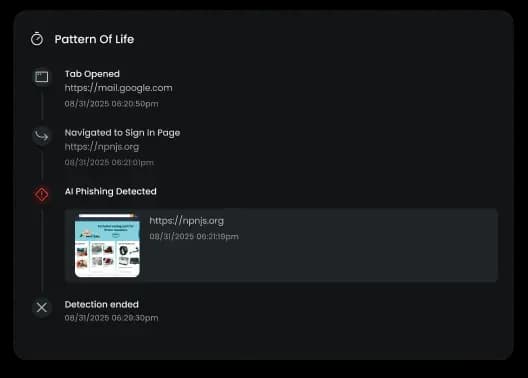
Real-World Example
A user receives a perfectly spoofed internal email linking to a fake payroll update form hosted on Dropbox. The email passes through email filters and lands in the inbox. With traditional tools, nothing stops the user from entering credentials. With Neon:
The browser detects a suspicious login pattern
It cross-checks the destination against known risk signals
The browser flags the session and blocks access in real time delivering a clear message that explains the risk
Result: No credential theft, no lateral movement, no alert fatigue.
See How Neon Catches What Email Security Misses
Speak with the experts on phishing prevention to learn what Neon can do for your team
